Running workloads on Google Kubernetes Engine (GKE) gives teams the ability to scale quickly, deploy efficiently, and build modern applications. But as containers become the standard unit of deployment, securing those containers becomes critical. It is not enough to focus on infrastructure security alone. The container images themselves must also be verified, trusted, and protected throughout the software delivery process.
Security threats targeting containerized environments are evolving. Attackers now exploit software supply chains, vulnerable base images, and misconfigured permissions. For this reason, it is important to build container security into each phase of the development and deployment lifecycle. GKE offers integrated tools to help achieve this.
In this article, we will walk through three important practices that form the foundation of container security in GKE. These practices are vulnerability scanning, attestations, and binary authorization. Each one builds on the previous and helps ensure that the container images you deploy are safe, compliant, and trustworthy.
Start with Vulnerability Scanning
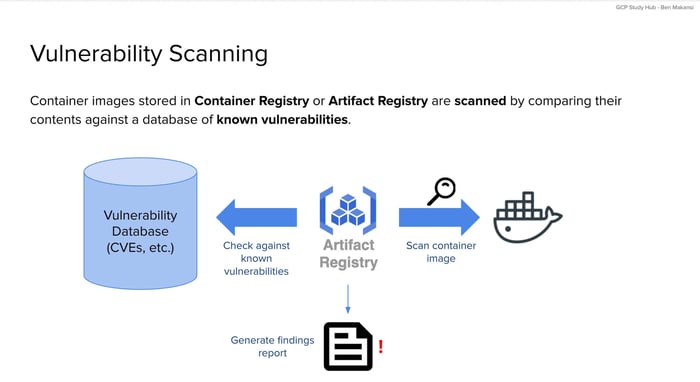
Security starts with visibility. Before deploying a container image, it is important to know what's inside it. GCP helps with this by automatically scanning container images stored in Container Registry or Artifact Registry. These are the two main places where GKE workloads store images.
The scanning process compares the contents of each image to a database of known vulnerabilities. This database includes entries such as Common Vulnerabilities and Exposures (CVEs), which are formally maintained identifiers for publicly known cybersecurity weaknesses. Each CVE provides a standardized way to describe and track specific types of security flaws. If any vulnerabilities from this database are found in the image, the scanner generates a report that lists them. The report includes the severity level of each issue and offers actionable recommendations for remediation.
This information allows teams to prioritize which issues to address first. Critical vulnerabilities that can be remotely exploited should be fixed immediately. Lower-risk issues can be tracked and resolved over time. By making these decisions based on data, teams can better manage risk and avoid unnecessary deployment delays.
By reviewing these reports before deploying, teams can catch problems early. This makes it easier to fix issues before they become risks in production. It also supports a more proactive approach to security. Instead of waiting for an incident, teams can prevent one by using only secure images.
Add Attestations to Establish Trust
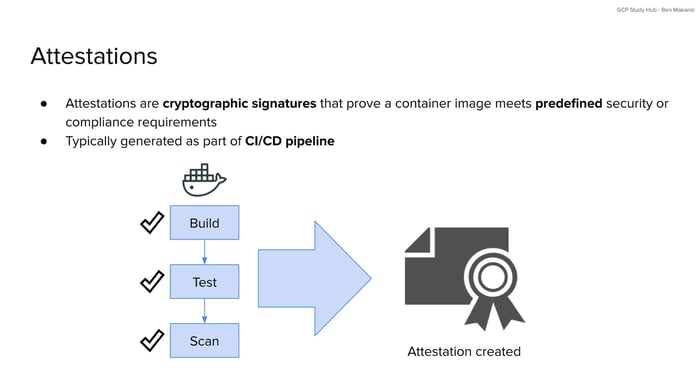
Once an image has been built, tested, and scanned, the next step is to prove that it passed all the required checks. This is where attestations come in. An attestation is a cryptographic signature that confirms the image has met certain predefined requirements. These requirements might include passing tests, completing scans, or following security policies.
Attestations are usually created as part of a CI/CD pipeline. After the pipeline finishes its steps, it signs the image to show that it followed the expected process. This signature can then be used later to verify that the image is safe to deploy.
Attestations are especially useful in larger organizations where many teams contribute to the same platform. By verifying images through automated pipelines, each team can demonstrate compliance without having to repeat manual reviews. This builds trust across environments and reduces the overhead of managing container integrity.
The main benefit of attestations is that they create a clear chain of trust. Teams no longer need to manually inspect or approve images. Instead, they can rely on automated checks and cryptographic proof. This reduces the risk of human error and helps enforce consistency across environments.
Use Binary Authorization to Enforce Policy
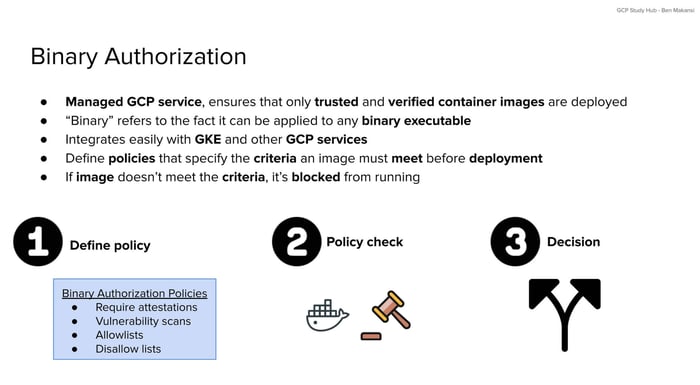
The final step in the security workflow is to enforce the policies that define which images are allowed to run. Binary Authorization is a managed service in GCP that does exactly this. It blocks the deployment of container images that do not meet your security requirements.
To use Binary Authorization, you begin by defining a policy. This policy can include several types of rules. You can require that images have attestations, that they pass vulnerability scans, or that they come from an approved list. You can also block certain images that you do not want deployed.
Binary Authorization evaluates each image just before it is deployed. This policy check happens automatically and does not slow down the deployment process. It simply ensures that images meet the rules your organization has defined.
When someone tries to deploy an image, Binary Authorization checks it against your policy. If the image meets all the rules, it is allowed to run. If it does not, the deployment is stopped. This prevents untrusted or insecure images from reaching your clusters.
Binary Authorization is especially useful in teams that work across multiple environments or projects. It ensures that the same rules apply everywhere. It also adds a final layer of control at the point of deployment.
Build a Secure Workflow from Start to Finish
Securing containerized workloads in GKE is not just about one tool or one step. It requires a complete workflow that starts with scanning, continues with validation, and ends with enforcement. Each part plays a role:
Vulnerability scanning identifies known risks in the image.
Attestations prove that the image passed all necessary checks.
Binary Authorization enforces policies and prevents unsafe deployments.
These three practices complement each other and should, for the most secure GKE deployments, be used together. Scanning alone can detect issues, but it does not stop unapproved images from running. Attestations can prove compliance, but they are only effective when policies are enforced. Binary Authorization provides that enforcement, but it depends on the data created by the earlier steps.
Together, they create a strong foundation for secure container deployments. They help teams move faster without sacrificing safety. They also support automation, reduce manual effort, and protect production systems from unexpected threats.
By following these best practices, you can deploy to GKE with greater confidence. You will know that every container image has been verified, trusted, and checked before it ever reaches your users.
Learn More
Google Kubernetes Engine, container security, and more are all essential concepts to understand for the Google Cloud Professional Cloud Architect (PCA) Certification Exam. I explore them in my PCA course if you would like to continue learning.