In many Google Cloud Platform (GCP) environments, especially those that involve multiple teams or departments, managing network infrastructure can become increasingly complex. Without a consistent structure, each project may independently configure its own network. This can lead to duplicated effort, inconsistent security policies, and fragmented administration. Over time, these issues may result in operational inefficiencies and increased risk.
Shared VPC, part of the Cloud VPC service in GCP, is designed to address these challenges. It allows network resources to be managed in a centralized way while still supporting the independence of individual projects. Through Shared VPC, multiple projects within the same GCP organization can connect to a single virtual network. This enables unified governance while maintaining clear boundaries between application development and infrastructure control.
Understanding Shared VPC
A Shared VPC allows one project, known as the Host Project, to own and administer a Virtual Private Cloud network. Other projects, known as Service Projects, are connected to this network. While the service projects manage their own GCP resources, such as virtual machines or Kubernetes clusters, the network environment is defined and maintained by the Host Project.
This model introduces a clear separation of concerns. Infrastructure teams can configure the network in the Host Project, while development teams can deploy and manage workloads in their respective service projects. This helps promote consistency and reduces the risk of configuration drift across projects.
Architecture and Workflow
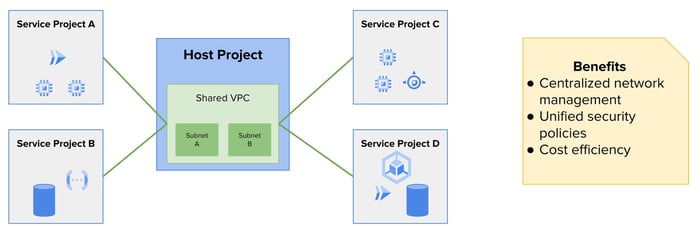
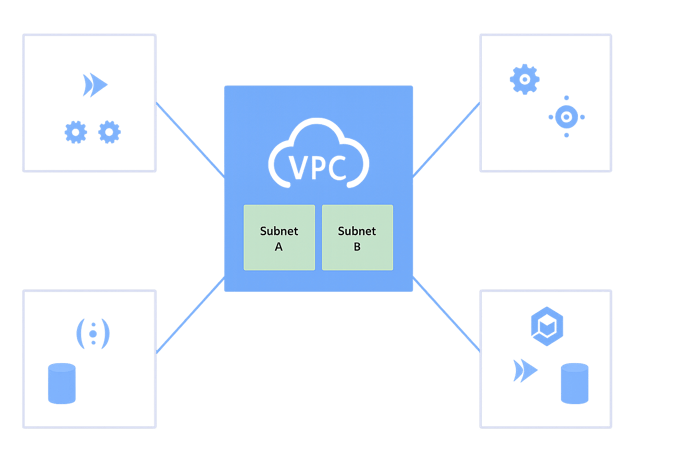
In this typical Shared VPC setup, the Host Project contains the shared Cloud VPC network and its subnets. For example, Subnet A and Subnet B might be defined within the host. Several service projects are then attached to this network. Each of these service projects can run different workloads, such as Cloud Run, Compute Engine, GKE, or Cloud Storage.
Although these workloads are deployed in separate projects, they communicate over the shared Cloud VPC. This arrangement simplifies internal service discovery and traffic routing. It also allows centralized firewall policies to be enforced uniformly across all connected workloads.
The key point is that network configuration is not repeated across projects. Instead, it is consolidated in the Host Project’s Cloud VPC. This reduces complexity and creates a more predictable environment for both networking and security teams.
Key Benefits of Shared VPC
One of the main benefits of Shared VPC is the ability to manage a single network configuration across many projects. This can help reduce the likelihood of human error. It also allows infrastructure teams to define standard practices that are applied consistently across the organization.
A second benefit is the ability to apply uniform security policies. Firewall rules, private access configurations, and routing policies can all be centrally defined. This provides a stable security baseline across all service projects. Because service projects cannot alter the core network configuration, there is less chance of unintentional changes that could affect connectivity or security posture.
A third advantage is improved resource efficiency. Infrastructure components such as load balancers, VPN gateways, or Cloud NAT can be shared across multiple service projects. This avoids duplication and can reduce operational overhead. It also simplifies billing and resource tracking by consolidating these components in a single project.
Use Cases
Shared VPC is particularly useful in organizations that have multiple GCP projects aligned with different teams or environments. For example, an enterprise might use a Shared Cloud VPC to connect development, staging, and production environments under a common network policy. This supports consistent behavior across environments without requiring repeated configuration.
Another common use case involves central infrastructure or platform teams managing Cloud VPC configurations on behalf of application teams. The infrastructure team can maintain the Host Project and control all routing and firewall rules. Application teams can continue to build and deploy services in their own projects without needing to manage the underlying network.
Organizations using multi-tenant architectures can also benefit. Separate customer environments may reside in different projects, while network services such as load balancing or monitoring tools are shared through a central Cloud VPC.
Operational Considerations
While Shared VPC offers a range of benefits, it does require deliberate planning and coordination. Subnet IP ranges must be carefully assigned to avoid conflicts. Quotas on network resources, such as the number of firewall rules or routes, still apply and must be monitored. These quotas can become especially relevant in environments with many connected service projects or frequent configuration changes.
IAM roles should be assigned thoughtfully. Network administrators need sufficient privileges to manage the VPC in the Host Project. At the same time, service project users must be granted only the permissions they need to manage their own resources. Overprovisioning access can introduce risks, while underprovisioning may disrupt workflows and delay development processes.
It is also important to enable appropriate logging and monitoring. Because traffic may flow across projects, visibility into flow logs and audit logs is essential for maintaining operational awareness and responding to incidents. Integrating this visibility into existing observability tools can help streamline monitoring across the organization.
Final Thoughts
Shared VPC, part of Cloud VPC in Google Cloud, is a practical approach to managing network infrastructure when multiple projects are involved. It offers a way to maintain consistent network behavior while supporting the independence of individual project teams. By separating infrastructure management from application development, it encourages clearer responsibilities and reduces the risk of misconfiguration.
This approach may not be necessary in small or tightly scoped environments. However, in larger organizations or those managing complex application portfolios, Shared VPC can provide a structured foundation for scalability and security.
When implemented carefully, Shared VPC can contribute to a more coherent and maintainable network architecture in Google Cloud.
Learn More
Shared VPC is necessary knowledge for several GCP certification exams, including the Associate Cloud Engineer exam and the Professional Cloud Architect exam. Here are links to my courses that can prepare you for each: